All Categories
Featured
Table of Contents
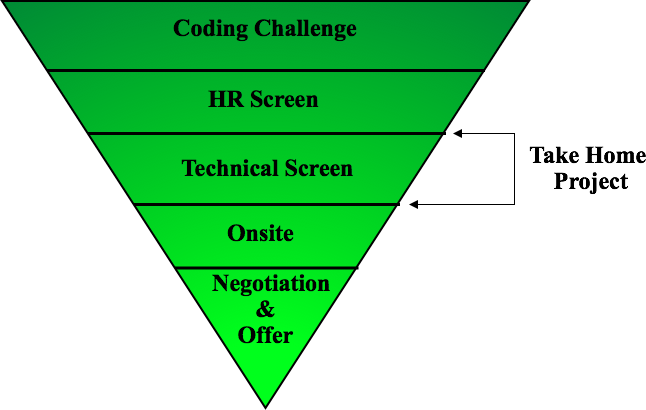
Amazon currently commonly asks interviewees to code in an online document data. This can vary; it could be on a physical white boards or a virtual one. Contact your recruiter what it will certainly be and practice it a great deal. Currently that you know what concerns to anticipate, allow's focus on exactly how to prepare.
Below is our four-step preparation prepare for Amazon data scientist candidates. If you're preparing for even more business than simply Amazon, after that examine our basic information scientific research meeting prep work guide. A lot of candidates stop working to do this. Yet before investing tens of hours getting ready for a meeting at Amazon, you need to take a while to make certain it's actually the right business for you.

, which, although it's developed around software application advancement, must offer you a concept of what they're looking out for.
Note that in the onsite rounds you'll likely have to code on a whiteboard without being able to perform it, so practice creating through problems on paper. Supplies totally free programs around initial and intermediate device discovering, as well as data cleaning, data visualization, SQL, and others.
Creating A Strategy For Data Science Interview Prep
You can upload your own inquiries and go over topics most likely to come up in your meeting on Reddit's statistics and artificial intelligence threads. For behavior interview inquiries, we suggest finding out our detailed approach for addressing behavior concerns. You can then use that technique to practice responding to the instance concerns offered in Section 3.3 above. Ensure you contend the very least one tale or example for every of the principles, from a broad variety of placements and jobs. A wonderful way to practice all of these different types of concerns is to interview on your own out loud. This might appear odd, but it will significantly improve the method you connect your answers during a meeting.

One of the major challenges of information researcher meetings at Amazon is connecting your various responses in a means that's very easy to comprehend. As an outcome, we strongly suggest exercising with a peer interviewing you.
Be alerted, as you may come up against the following problems It's difficult to recognize if the comments you obtain is precise. They're not likely to have insider expertise of interviews at your target firm. On peer platforms, individuals often squander your time by not showing up. For these factors, several candidates skip peer simulated interviews and go right to mock meetings with an expert.
Tackling Technical Challenges For Data Science Roles

That's an ROI of 100x!.
Information Scientific research is rather a big and varied area. Because of this, it is truly tough to be a jack of all trades. Commonly, Data Science would certainly focus on mathematics, computer system scientific research and domain name competence. While I will briefly cover some computer technology fundamentals, the bulk of this blog will primarily cover the mathematical fundamentals one might either need to review (or even take a whole program).
While I understand a lot of you reading this are a lot more mathematics heavy by nature, recognize the mass of data science (risk I claim 80%+) is collecting, cleaning and processing data into a helpful type. Python and R are one of the most preferred ones in the Data Science space. I have additionally come throughout C/C++, Java and Scala.
Best Tools For Practicing Data Science Interviews

Typical Python collections of selection are matplotlib, numpy, pandas and scikit-learn. It prevails to see most of the information scientists remaining in a couple of camps: Mathematicians and Database Architects. If you are the 2nd one, the blog won't aid you much (YOU ARE ALREADY AMAZING!). If you are among the very first group (like me), opportunities are you really feel that composing a dual embedded SQL inquiry is an utter nightmare.
This may either be collecting sensor information, analyzing web sites or accomplishing surveys. After collecting the information, it requires to be changed into a functional form (e.g. key-value shop in JSON Lines data). As soon as the data is accumulated and placed in a useful style, it is necessary to perform some data high quality checks.
Facebook Data Science Interview Preparation
In situations of fraud, it is extremely usual to have hefty course discrepancy (e.g. only 2% of the dataset is real scams). Such details is essential to select the ideal options for attribute design, modelling and design examination. For additional information, examine my blog site on Scams Detection Under Extreme Course Discrepancy.
In bivariate evaluation, each feature is compared to various other functions in the dataset. Scatter matrices enable us to discover concealed patterns such as- functions that should be crafted together- features that may need to be eliminated to prevent multicolinearityMulticollinearity is really a problem for several versions like linear regression and for this reason needs to be taken treatment of accordingly.
In this section, we will certainly discover some typical feature design techniques. Sometimes, the function by itself might not supply useful details. Think of making use of internet use information. You will certainly have YouTube users going as high as Giga Bytes while Facebook Carrier customers use a couple of Huge Bytes.
Another issue is using specific values. While categorical values prevail in the information science world, understand computers can only comprehend numbers. In order for the categorical worths to make mathematical sense, it requires to be changed right into something numeric. Generally for specific worths, it prevails to carry out a One Hot Encoding.
Faang Interview Preparation Course
At times, having also several sporadic dimensions will hamper the performance of the design. A formula typically utilized for dimensionality decrease is Principal Components Analysis or PCA.
The common groups and their sub categories are explained in this area. Filter methods are normally utilized as a preprocessing step. The choice of attributes is independent of any equipment finding out formulas. Rather, attributes are picked on the basis of their scores in numerous analytical tests for their relationship with the result variable.
Common techniques under this category are Pearson's Correlation, Linear Discriminant Analysis, ANOVA and Chi-Square. In wrapper approaches, we attempt to make use of a subset of attributes and educate a design utilizing them. Based upon the inferences that we attract from the previous version, we decide to add or eliminate attributes from your subset.
Algoexpert
These approaches are generally computationally extremely pricey. Usual methods under this group are Forward Choice, Backward Removal and Recursive Feature Removal. Installed techniques combine the top qualities' of filter and wrapper approaches. It's implemented by algorithms that have their very own built-in function selection methods. LASSO and RIDGE are common ones. The regularizations are given up the equations listed below as referral: Lasso: Ridge: That being said, it is to understand the mechanics behind LASSO and RIDGE for meetings.
Not being watched Understanding is when the tags are inaccessible. That being claimed,!!! This blunder is sufficient for the recruiter to terminate the meeting. Another noob blunder people make is not stabilizing the functions prior to running the version.
Thus. Guideline of Thumb. Linear and Logistic Regression are one of the most basic and commonly used Machine Discovering algorithms around. Before doing any type of evaluation One typical meeting bungle people make is starting their evaluation with a more complex design like Semantic network. No uncertainty, Neural Network is highly exact. Nevertheless, standards are very important.
Table of Contents
Latest Posts
How To Answer System Design Interview Questions – A Step-by-step Guide
Back-end Engineering Interview Guide – What To Expect
Common Mistakes To Avoid In A Software Engineer Behavioral Interview
More
Latest Posts
How To Answer System Design Interview Questions – A Step-by-step Guide
Back-end Engineering Interview Guide – What To Expect
Common Mistakes To Avoid In A Software Engineer Behavioral Interview